Security news
Security
DeFake tool protects voice recordings from cybercriminals
In what has become a familiar refrain when discussing artificial intelligence (AI)-enabled technologies, voice cloning makes possible beneficial advances in accessibility and creativity while also enabling increasingly sophisticated ...
21 hours ago
0
1
Computer Sciences
Linkable and traceable anonymous authentication with fine-grained access control
Anonymous authentication plays a crucial role in privacy-focused applications, and it is used for authenticating a user's identity in a privacy-preserving way. If enough privacy is provided, malicious users may misuse privacy. ...
Apr 19, 2024
0
8

UK police say they disrupted cyber fraud network that stole personal data from thousands
A website that allowed international cyber fraudsters to trick up to 70,000 British victims into revealing personal information such as bank account details and passwords has been infiltrated and disrupted, London police ...
Apr 18, 2024
0
0

Colorado law protects brain data captured by gadgets
Colorado on Wednesday expanded its privacy law to include brain data gathered by the booming array of gadgets people use for feedback about sleep, fitness, sports, and lifestyle.
Apr 18, 2024
0
13

Russian 'cyber sabotage' a global threat: Security firm
A cyber group with links to Russian military intelligence is set to become a significant global threat after playing an increasing critical role in the ongoing conflict in Ukraine, a leading cybersecurity firm warned Wednesday.
Apr 18, 2024
0
11
Internet
AI is making smart devices easier to hack—here's how to stay safe
From asking our smart speakers for the weather to receiving personalized advice from smartwatches, devices powered by artificial intelligence (AI) are increasingly streamlining our routines and decision making. The technology ...
Apr 17, 2024
0
21
Internet
Websites deceive users by deliberately hiding the extent of data collection and sharing
Websites sometimes hide how widely they share our personal information, and can go to great lengths to pull the wool over our eyes. This deception is intended to prevent full disclosure to consumers, thus preventing informed ...
Apr 17, 2024
0
12
Security

Paris faces cyber battle to keep Games running and real
The Paris Olympics are bracing themselves to fight off an unprecedented level of cyber attacks, for the first time augmented by artificial intelligence.
Apr 16, 2024
0
1
Business

Atrium Health shared patient data with Facebook, class-action lawsuit alleges
A class-action lawsuit filed in North Carolina accuses Atrium Health of allowing Facebook and Google to access patient information online to use in targeted ads.
Apr 16, 2024
0
14
Internet

Security vulnerability in browser interface allows computer access via graphics card
Modern websites place ever greater demands on the computing power of computers. For this reason, web browsers have also had access to the computing capacities of the graphics card (Graphics Processing Unit or GPU) in addition ...
Apr 15, 2024
0
36
Internet

Safeguarding the future of online security with AI and metasurfaces
Researchers at Pohang University of Science and Technology (POSTECH) have advanced online security by integrating an AI-based metasurface with oblique helicoidal cholesteric liquid crystals.
Apr 15, 2024
0
21
Business

Microsoft, beset by hacks, grapples with problem years in the making
The world's largest seller of cybersecurity products has a problem with its own cybersecurity.
Apr 15, 2024
0
3
Security

Israel using AI to identify human targets raising fears that innocents are being caught in the net
A report by Jerusalem-based investigative journalists published in +972 magazine finds that AI targeting systems have played a key role in identifying—and potentially misidentifying—tens of thousands of targets in Gaza. ...
Apr 15, 2024
0
17
Internet

US House okays renewal of controversial surveillance program
The US House of Representatives voted Friday to reauthorize an electronic surveillance program targeting foreigners, a practice officials say is critical to national security but criticized by opponents over concerns for ...
Apr 13, 2024
0
23
Security

Will AI be listening in on your future job interview? On law, technology and privacy
The law and Artificial Intelligence (AI) applications need to be better aligned to ensure our personal data and privacy are protected. Ph.D. candidate Andreas Häuselmann can see opportunities with AI, but dangers if this ...
Apr 11, 2024
0
11
Security

World-first 'Cybercrime Index' ranks countries by cybercrime threat level
Following three years of intensive research, an international team of researchers have compiled the first ever "World Cybercrime Index," which identifies the globe's key cybercrime hotspots by ranking the most significant ...
Apr 10, 2024
0
22
Security
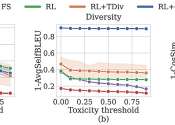
Researchers find a faster, better way to prevent an AI chatbot from giving toxic responses
A user could ask ChatGPT to write a computer program or summarize an article, and the AI chatbot would likely be able to generate useful code or write a cogent synopsis. However, someone could also ask for instructions to ...
Apr 10, 2024
0
34